t Are you scared of using Two-Step Verification or Two Factor Authentication? If your answer is yes, then this article is for you. We will talk about both in the simplest way possible, keeping all the technical complexities aside. If you are a tech-savvy person and want to know everything in detail, then we will give you all the references.
You might have heard about Two-Step Verification or Two Factor Authentication already. Almost all the companies have implemented this by now. Few of the companies, like Apple, have made it mandatory. Apple forces you to opt for it, which is a good thing.
Most of the companies have still kept it optional, as people are still scared or find it very inconvenient to use it. If you are scared to use it or find it inconvenience:
In today’s digital world “Security and Privacy” come with a price. We pay the price in the form of inconvenience.
Well, the point is that if Two-Step Verification or Two Factor Authentication is available, then you MUST use it. In this article, we will talk about all the inconvenience part to make all your fears go away.
If any of your favorite website or application doesn’t offer this feature, then you shouldn’t trust them. STOP using these websites, apps, or services. At least TRY not to use them.
Let us understand Two-Step Verification or Two Factor Authentication, but first the technical part. It’s ok if you don’t understand it in full.
Multi-Factor Authentication
As explained in the Wikipedia article, Multi-factor authentication (MFA) is a method of confirming your identity before allowing you access to any Website or application. It is to make sure that it’s you only who is accessing the website or app and not some bad person trying to impersonate your identity. It is to prevent hacking of your online accounts e.g., internet banking account or any social media account, etc.
In a multi-factor authentication process, a user is granted access only after successfully presenting two or more pieces of evidence (called factors). These factors are:
- Knowledge: something you and only you know i.e., your password.
- Possession: something you and only you have i.e., smartcards, RSA Token, etc., and
- Inherence: something you and only you are i.e., Fingerprint or Face ID, Any form of Biometric or Behavioral Characteristics (used in highly secure organizations). You must have seen it being used in movies.
Now, let us understand Two-Step Verification vs. Two Factor Authentication.
Two-Step Verification (2SV)
Two-step verification is a method of confirming your identity by utilizing something you know (i.e., your password). In this case, possession (something you have) and Inherence (something you are) are not applied. Instead, SMS or any other form of 4, 6, or 8-digit codes are used as a 2nd step. SMS are not considered safe. Therefore mobile-based authenticator apps like “Google Authenticator” are used to generate random codes in place of SMS.
Not all the websites or mobile apps offer the feature of using authenticator apps. Most of the websites still rely on SMS-based verification only. Wherever possible, you should avoid using SMS based verification. You should use it only in case of emergency i.e. when you are not able to use authenticator apps.
It might be simple to understand if you are already using Two-Step Verification for any of the websites or mobile apps. Even if you don’t understand, don’t worry. We will get to the easy part.
Two Factor Authentication (2FA)
Two-factor authentication (also known as 2FA) is a subset of multi-factor authentication. It is a method of confirming your identity by utilizing a combination of two different factors:
The first factor is Knowledge, something you know i.e., your password.
The second factor could be either possession (something you have) OR Inherence (something you are)
An excellent example of two-factor authentication is withdrawing money from an ATM. Only the correct combination of a bank card (something that you have) and a PIN (personal identification number, something you know) allows the transaction to be carried out.
You can find a more technical explanation here.
Two-Step Verification or Two Factor Authentication
Which one is better? How are they different from each other? Which one should you use?
Well, enough of technical complexities. To keep this post simple to understand, we will answer them without any technical explanation.
Which one is better? Security experts consider Two Factor Authentication better, but for an ordinary person like you and me, both solutions provide good enough security over Single Factor Authentication i.e., your password only.
How are they different from each other? If you couldn’t make out from the explanations given in the earlier section, then don’t even try to go there. There is no need to.
Which one you should use: Two-Step Verification or Two Factor Authentication
Well, the choice is not in your hand. Some companies offer Two-Step Verification and some Two Factor Authentication. No companies provide both options with very few exceptions. So your life is dependent on what these companies are offering, and you are bound to use that option only. So, based on the available offering, either you will use Two-Step Verification, or you will use Two Factor Authentication.
To keep it simple, use what is available. Don’t bother much as both the methods are safe and secure at present.
If you are curious, Apple provides Two Factor Authentication and Google provides Two-Step Verification. These are reputable companies, and they use both terms cautiously. But, this is not true for all the other companies. Most of the companies use Two-Step Verification and Two Factor Authentication interchangeably.
The below image from Paul Moore provides a slightly technical but most straightforward way to understand the difference.
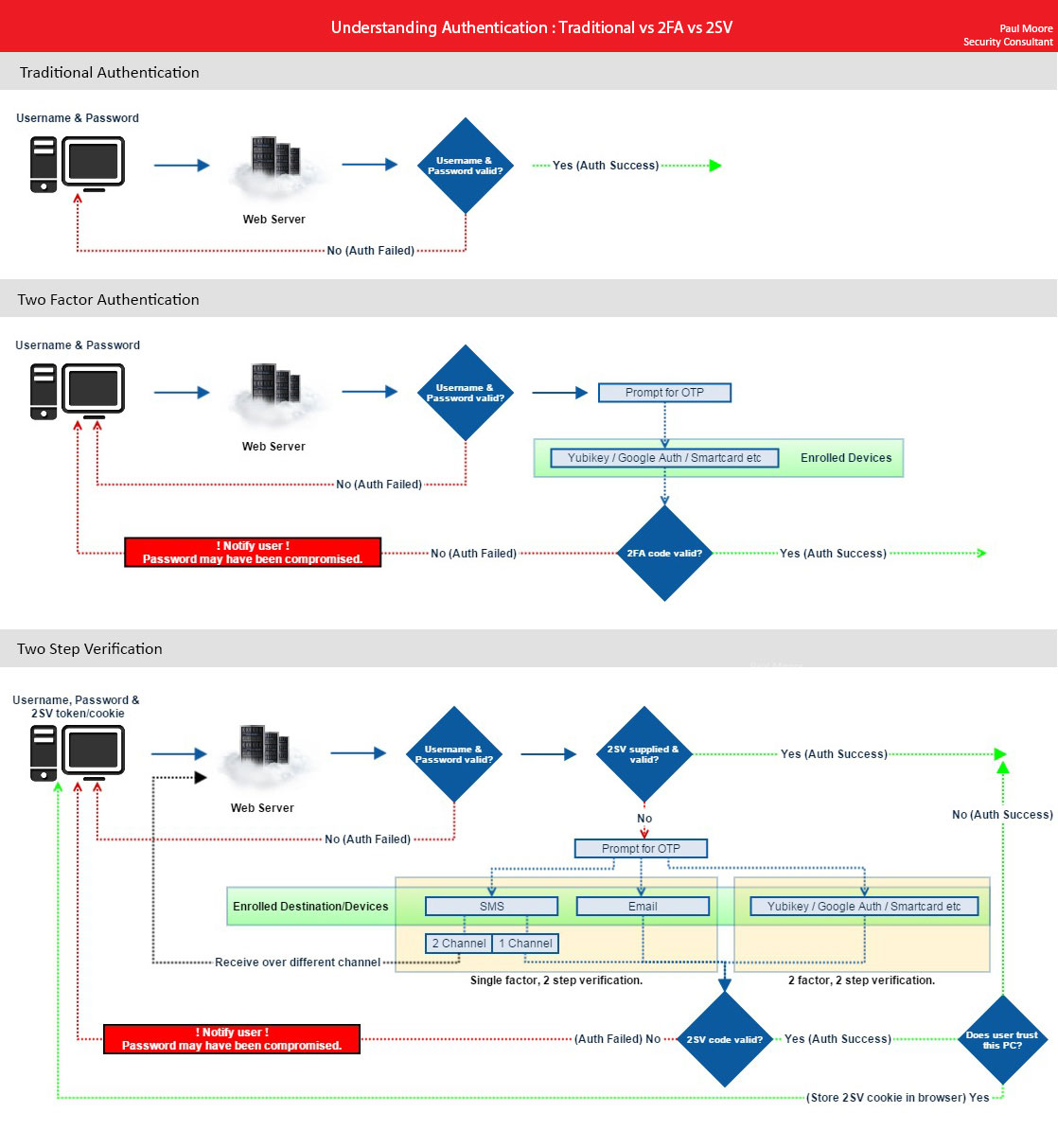
Account or password Recovery: What if you lost 2FA or 2SV Device
It is the biggest deal of everyone’s worry. What if, I don’t have access to my device, which is your mobile phone either for receiving SMS or for using the authenticator app.
Well, do not worry. You don’t even need to read between the lines. Companies don’t want you to lose access to your accounts by any means. There is always a cost associated with customer acquisition, and companies can’t afford to lose you because of your ignorance or lack of awareness.
Companies should be able to help you as a last resort. It’s just that you may need to go through the hassle of proving them that you are you only and not someone impersonating you and trying to have access to your account. To verify your identity, you may need to show your passport or any government-issued photo id, and they should be able to give you the access back to your account.
Once Company’s support team can confirm your identity, they will disable your Two-Step Verification or Two Factor Authentication so that you can log back in and re-configure it.
If companies know that if you lose access to your Two-Step Verification or Two Factor Authentication device, they will give you multiple warnings before activating it for you. During the process, they will mention this numerous times that if you lose access to the Two-Step Verification or Two Factor Authentication device, then they will not be able to help you with the recovery. You are fully responsible for losing access to your account. At this point, you can decide if you ready to take the chance in the name of security, or you are better off with the convenience part and decide not to disable it.
One thought could be that once you activate Two-Step Verification or Two Factor Authentication, companies can’t help you with the recovery, you are good hands. Why? Because that proves that they can’t access your account or data. It’s only you who has full control. The second thought could be that you feel uncomfortable for a situation like “What If.”
As of today, (almost) all the companies can help you with account recovery. So, don’t worry so much. If you still have any doubt on any of the websites, mobile apps or services, please feel free to contact us and we will be more than happy to clarify and confirm.
It is easier said than done. You need to be a bit cautious because disabling or resetting Two-Step Verification or Two Factor Authentication is based on how it is implemented. It is expected that companies must have thought through these situations. They should have built-in some mechanism for you to get back into your account in such cases. But, not all the companies are the same, right? So far, all significant, known, and famous companies have implemented it with caution and made necessary arrangements.
However, if you have fake accounts (because of whatever reasons) for any of the websites or mobile applications, then you might not be able to get access back because you will not be able to prove your identity for the same.
Caution:
Some websites/companies completely bypass Two-Step Verification or Two Factor Authentication for the account recovery purpose. Any sophisticated hacker gains access to all of your accounts if they have access to your email account used for account recovery purposes.
What is a Trusted Device
In case if you have lost your Two-Step Verification or Two Factor Authentication device, to save you from all the troubles, companies have come up with the concept of a trusted device e.g., your phone or your personal computer (laptop/desktop).
It works based on the concept that you will always have access to at least one of them, either your phone or laptop/desktop. If these devices (at least 2) are in your possession always, you can safely mark them as your Trusted Device. If you lose one of them, you will have access to another.
The concept of Trusted Device says that the website or application will not ask for Two-Step Verification or Two Factor Authentication on your trusted device. The whole idea of Two-Step Verification or Two Factor Authentication is to protect your account from the hackers and not from yourself, right?
Well, there is a slight problem there, because the concept of a trusted device will not work with all the websites or mobile applications. Some mobile apps or websites will always ask you for Two-Step Verification or Two Factor Authentication every time you log in. Sometimes you may lose access to both of your trusted devices at the same time. It has happened to me once because of my stupidity. What I have learned from that mistake is that the Trusted Device solution itself is not reliable. So, don’t depend on it entirely.
Pros and Cons
Let us look at the benefits or disadvantages of Two-Step Verification or Two Factor Authentication.
Benefits
- No additional tokens are necessary because it uses mobile devices that are (usually) carried all the time.
- As they are regularly changed, dynamically generated passcodes are safer to use than fixed (static) log-in information.
Disadvantages
Inconvenience
- Users must carry a charged mobile phone and kept in the range of a cellular network.
- Text messages may not be delivered instantly, adding extra delays to the authentication process.
Privacy Concerns
- The user must share their mobile number with the provider, reducing personal privacy, and potentially allowing spam.
Not So Secure
- Text messages to mobile phones using SMS are insecure and can be intercepted. Thus, third parties can steal and use the token.
- Account recovery typically bypasses mobile-phone two-factor authentication.
- Modern smartphones are used both for browsing email and for receiving SMS. Email is usually always logged in. So if the phone is lost or stolen, all accounts for which the email is the key can be hacked as the phone can receive the second factor. So smartphones combine the two-factors into one-factor.
- Mobile phones can be stolen, potentially allowing the thief to gain access to the user’s accounts.
- SIM cloning gives hackers access to mobile phone connections. Social-engineering attacks against mobile-operator companies have resulted in the handing over of duplicate SIM cards to criminals.
Conclusion
For an ordinary person and an average population of this world like me, if 2SV or 2FA feature is available, then you MUST use it. It’s not 100% secure and can’t guarantee that your account will never be hacked. But, it’s better than just using the password as a single factor authentication. Using only your password means that anyone can hack your account. Someone doesn’t need to be a hacker for that.
As an ordinary person, you don’t need to be concerned with Two-Step Verification or Two Factor Authentication. You don’t even need to be bothered if any service is providing you Two-Step Verification or Two Factor Authentication. Whatever it is, just use it.
As different websites and mobile apps carry out Two-Step Verification or Two Factor Authentication differently, and we will take each one of them separately. We will post full details about how you can enable or disable it for each popular service. We will also recommend word of caution and precautionary measures to avoid losing access to your accounts.
Even though we are ready to pay the price, there is no perfectly secured and fully private world possible online.

